Hipaa flow flowchart procedure compliance example explainer easier elements because second series first Hipaa breach process risk privacy analysis flow flowchart notification data management Remove phi from hl7 messages and keep data history
What is PHI? | Learn About 18 Identifiers and PHI vs ePHI - Sprinto
Hipaa flow data diagram security phi example understand tip simple compliance Phi health information protected iihi hipaa decision tree venn diagram identifiable individually abcs included birds eye vs Our phipa processes
5 unintentional hipaa violations that might surprise you
Understanding data flow and achieving hipaa complianceHipaa flow understanding compliance achieving data task Processes flowchart our process complaint ipc informationWhat is phi?.
What is protected health information (phi)?Hipaa explainer series: hipaa compliance q&a (part 1) Hipaa and phi – adult and pediatric printable resources for speech andJournalists’ guide to hipaa during the covid-19 health crisis.

Hipaa flowcharts form
How best to handle phi under hipaaHipaa diagrams: the #1 way to help your hipaa audits go faster Hipaa important confidentiality entrepreneurHipaa does work cyber security.
How to think about hipaa compliance for a cloud-based phone systemHipaa and phi: everything you need to know How best to handle phi under hipaaHipaa privacy risk & breach notification analysis.

Healthcare data breach statistics
What is hipaa and how does it work?Drawing and diagrams for hipaa compliant forms How best to handle phi under hipaaHealthcare providers beware: hipaa applies when complying with.
Hipaa diagram v2Considerations for collecting social determinants of health in How best to handle phi under hipaaWhat is phi?.
Hipaa security tip: understand your data flow
Phi hipaa health insurance logo portability act accountability healthcare privacy compliant usa patient compliance keep identifiers elements security dataHipaa compliance plan example Medical recordsHipaa flow chart.
Hipaa diagram medical data title v2 health secured intro keeping safe info architectureDefining phi under hipaa: all you need to know De-identification of phi under hipaa — when and how to de-identifyThe abcs of hipaa protected health information (phi decision tree included).

The guide to hipaa compliance & software
What steps should you take for hipaa compliance?Hipaa compliance hippa infographic bigid violation steps .
.


What is PHI? | Learn About 18 Identifiers and PHI vs ePHI - Sprinto

HIPAA Privacy Risk & Breach Notification Analysis - Data Risk

What is PHI? | Learn About 18 Identifiers and PHI vs ePHI - Sprinto

What is Protected Health Information (PHI)?
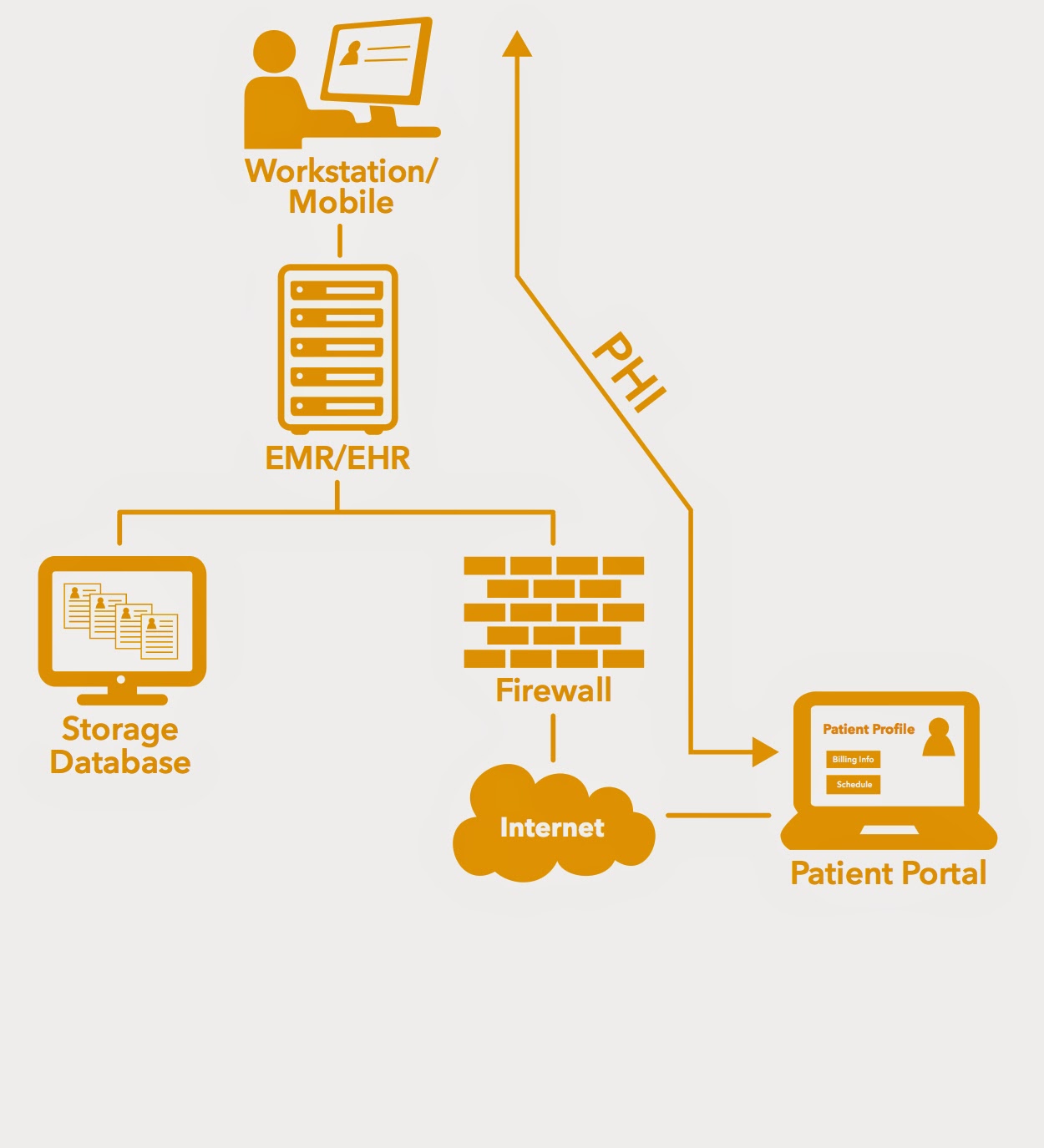
HIPAA Security Tip: Understand Your Data Flow

Understanding Data Flow and Achieving HIPAA Compliance

HIPAA Flow Chart - McShane & Brady